1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
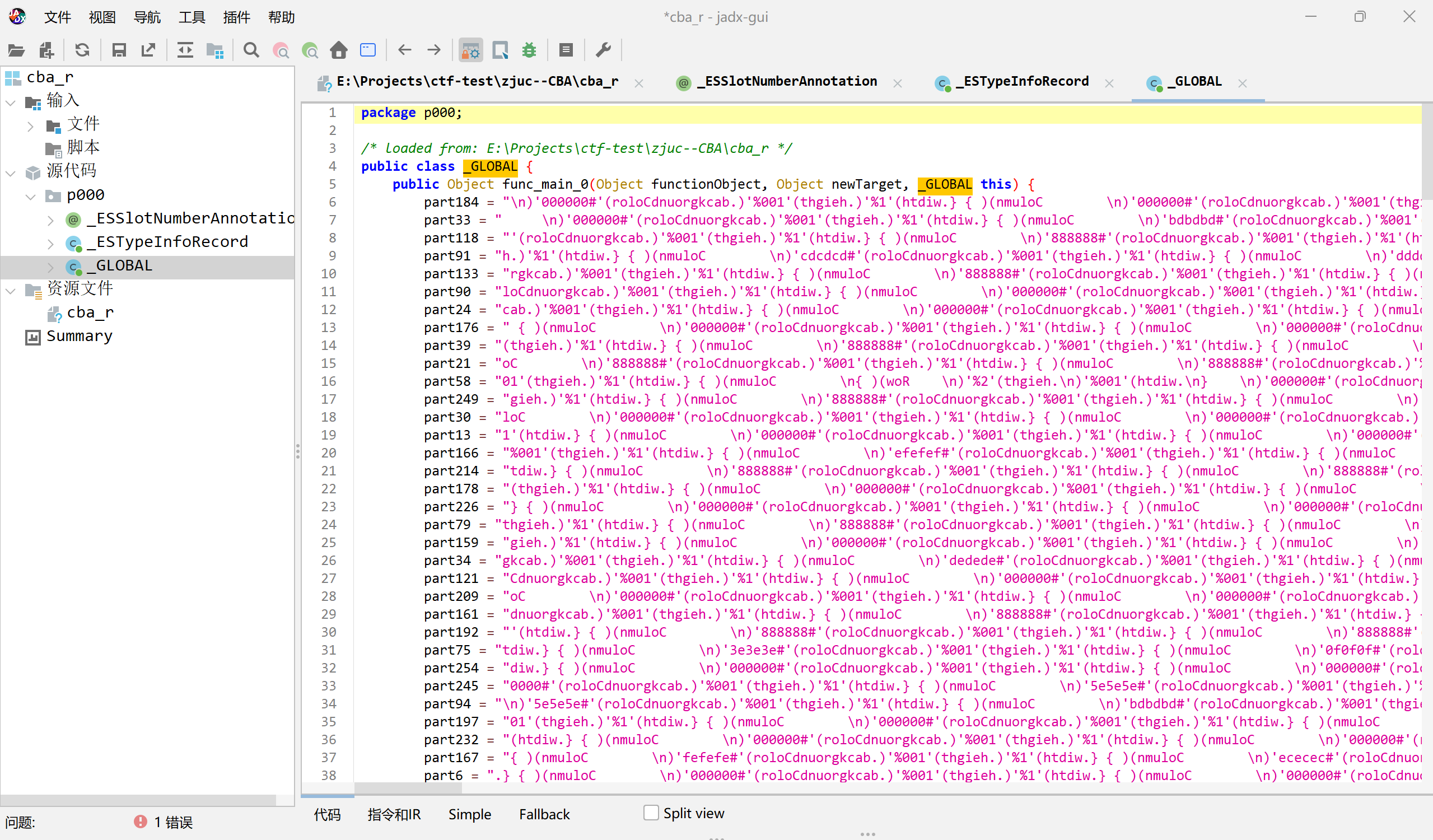
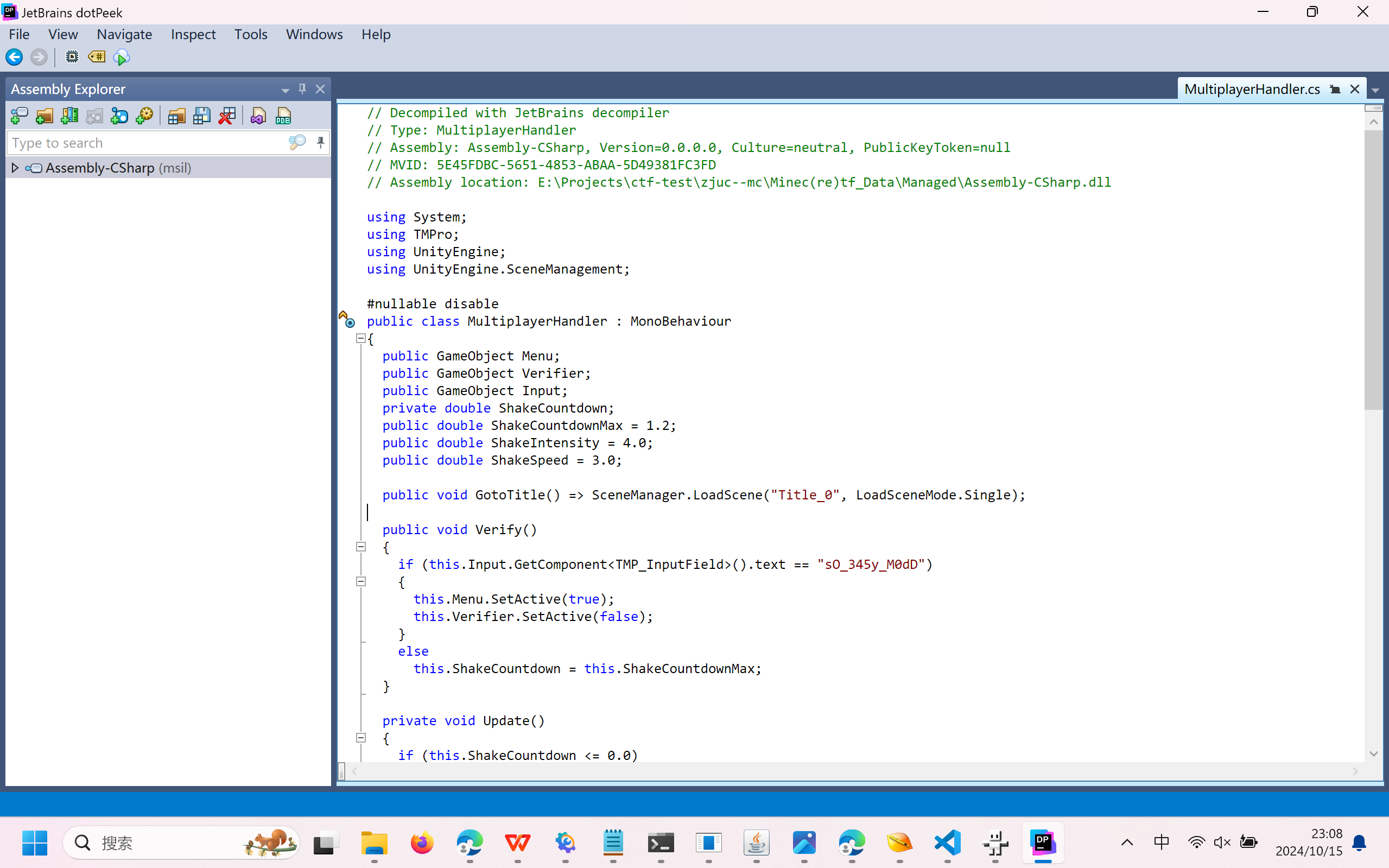
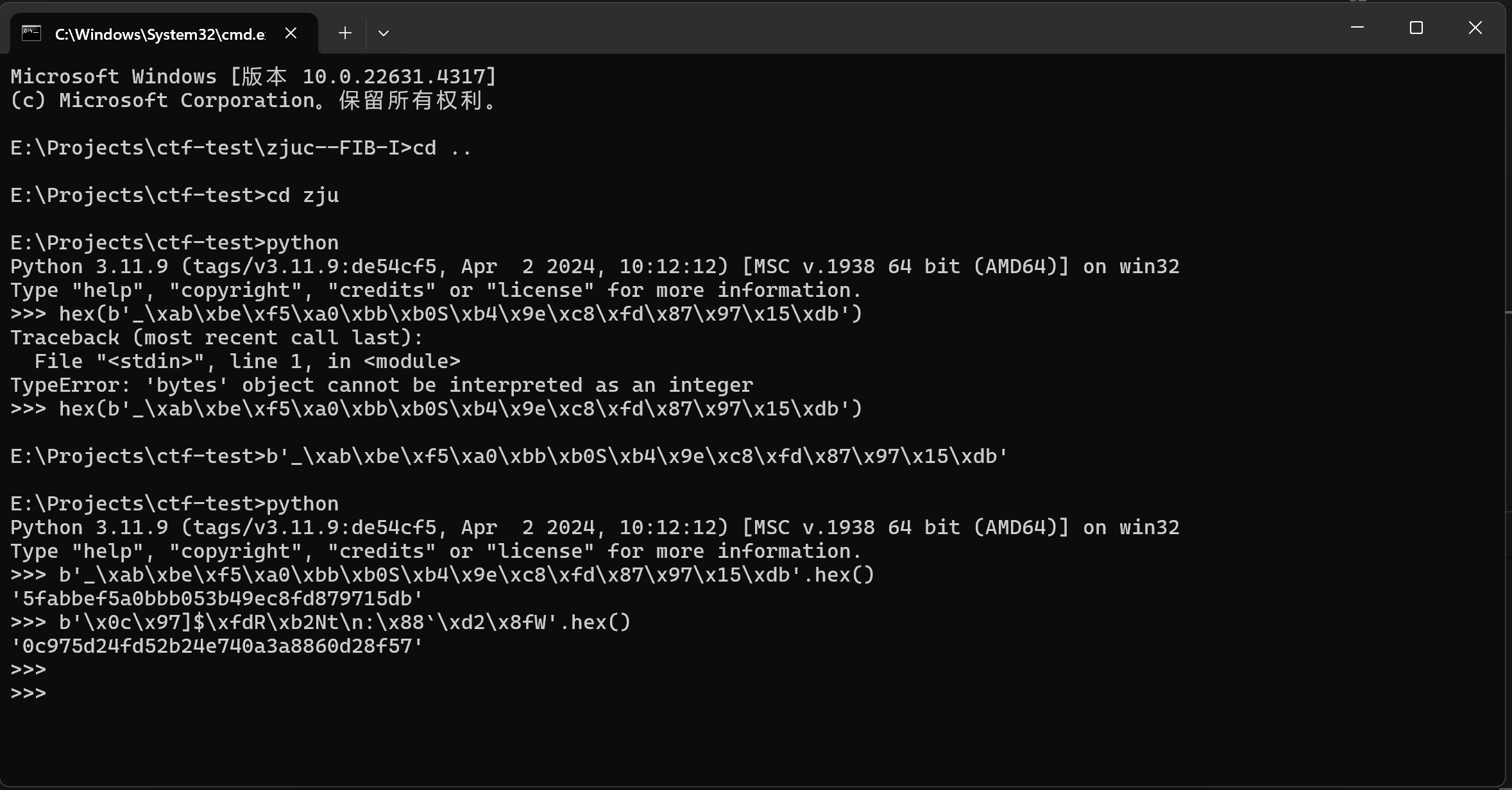
| class CipherUtil {
public Object f0pkgNameentry;
public Object isCommonjs;
public Object moduleRecordIdx;
public Object #1#(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
Object obj = _lexenv_0_2_.cipherX;
Object init = obj.init(import { default as cryptoFramework } from "@ohos:security.cryptoFramework".CryptoMode.ENCRYPT_MODE, arg0, 0);
return init.then(#2#);
}
public Object #2#(Object functionObject, Object newTarget, CipherUtil this) {
Object obj = _lexenv_0_2_.cipherX;
return obj.doFinal(_lexenv_0_0_);
}
public Object #3#(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
Object obj = _lexenv_0_3_.cipherY;
Object init = obj.init(import { default as cryptoFramework } from "@ohos:security.cryptoFramework".CryptoMode.ENCRYPT_MODE, arg0, _lexenv_0_0_);
return init.then(#4#);
}
public Object #4#(Object functionObject, Object newTarget, CipherUtil this) {
Object obj = _lexenv_0_3_.cipherY;
return obj.doFinal(_lexenv_0_1_);
}
public Object #5#(Object functionObject, Object newTarget, CipherUtil this, Object arg0, Object arg1) {
arg0("");
return null;
}
public Object #6#(Object functionObject, Object newTarget, CipherUtil this, Object arg0, Object arg1) {
newlexenv(1);
_lexenv_0_0_ = arg0;
Object ldlexvar = _lexenv_1_5_;
Object encryptX = ldlexvar.encryptX(_lexenv_1_0_);
encryptX.then(#7#);
return null;
}
public Object #7#(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
_lexenv_1_1_ = arg0.data;
Object ldlexvar = _lexenv_1_5_;
Object encryptY = ldlexvar.encryptY(_lexenv_1_2_, _lexenv_1_1_);
encryptY.then(#8#);
return null;
}
public Object #8#(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
_lexenv_1_3_ = arg0.data;
Object ldlexvar = _lexenv_1_5_;
Object encodeX = ldlexvar.encodeX(_lexenv_1_1_, _lexenv_1_3_);
Object ldlexvar2 = _lexenv_1_5_;
_lexenv_0_0_(ldlexvar2.encodeY(encodeX));
return null;
}
public Object init(Object functionObject, Object newTarget, CipherUtil this) {
Object cryptoFramework = import { default as cryptoFramework } from "@ohos:security.cryptoFramework";
this.cipherX = cryptoFramework.createCipher(this.cipherAlgX);
Object cryptoFramework2 = import { default as cryptoFramework } from "@ohos:security.cryptoFramework";
this.cipherY = cryptoFramework2.createCipher(this.cipherAlgY);
Object obj = createobjectwithbuffer(["data", 0]);
obj.data = this.stringToUint8Array(this.commonCipherKeyStr);
this.commonCipherKey = obj;
return null;
}
public Object encodeX(Object functionObject, Object newTarget, CipherUtil this, Object arg0, Object arg1) {
Object[] objArr = [Object];
for (int i = 0; isfalse((i < 16 ? 1 : 0)) == null; i++) {
objArr.push(arg0[i] ^ arg1[i]);
}
for (int i2 = 0; isfalse((i2 < 16 ? 1 : 0)) == null; i2++) {
objArr.push(arg1[i2]);
}
return Uint8Array(objArr);
}
public Object encodeY(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
Object newobjrange = import { default as util } from "@ohos:util".Base64Helper();
return newobjrange.encodeToStringSync(arg0);
}
public Object encrypt(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
newlexenv(6);
_lexenv_0_4_ = newTarget;
_lexenv_0_5_ = this;
_lexenv_0_3_ = null;
_lexenv_0_1_ = null;
if (isfalse((arg0.length != 32 ? 1 : 0)) == null) {
return Promise(#5#);
}
Object ldlexvar = _lexenv_0_5_;
_lexenv_0_0_ = ldlexvar.stringToUint8Array(arg0.slice(0, 16));
Object ldlexvar2 = _lexenv_0_5_;
_lexenv_0_2_ = ldlexvar2.stringToUint8Array(arg0.slice(16, 32));
return Promise(#6#);
}
public Object encryptX(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
newlexenv(3);
_lexenv_0_1_ = newTarget;
_lexenv_0_2_ = this;
Object obj = createobjectwithbuffer(["data", 0]);
obj.data = arg0;
_lexenv_0_0_ = obj;
Object cryptoFramework = import { default as cryptoFramework } from "@ohos:security.cryptoFramework";
Object createSymKeyGenerator = cryptoFramework.createSymKeyGenerator(_lexenv_0_2_.cipherAlgName);
Object convertKey = createSymKeyGenerator.convertKey(_lexenv_0_2_.commonCipherKey);
return convertKey.then(#1#);
}
public Object encryptY(Object functionObject, Object newTarget, CipherUtil this, Object arg0, Object arg1) {
newlexenv(4);
_lexenv_0_2_ = newTarget;
_lexenv_0_3_ = this;
Object obj = createobjectwithbuffer(["data", 0]);
obj.data = arg0;
_lexenv_0_1_ = obj;
Object obj2 = createobjectwithbuffer(["algName", "IvParamsSpec", "iv", 0]);
Object obj3 = createobjectwithbuffer(["data", 0]);
obj3.data = arg1;
obj2.iv = obj3;
_lexenv_0_0_ = obj2;
Object cryptoFramework = import { default as cryptoFramework } from "@ohos:security.cryptoFramework";
Object createSymKeyGenerator = cryptoFramework.createSymKeyGenerator(_lexenv_0_3_.cipherAlgName);
Object convertKey = createSymKeyGenerator.convertKey(_lexenv_0_3_.commonCipherKey);
return convertKey.then(#3#);
}
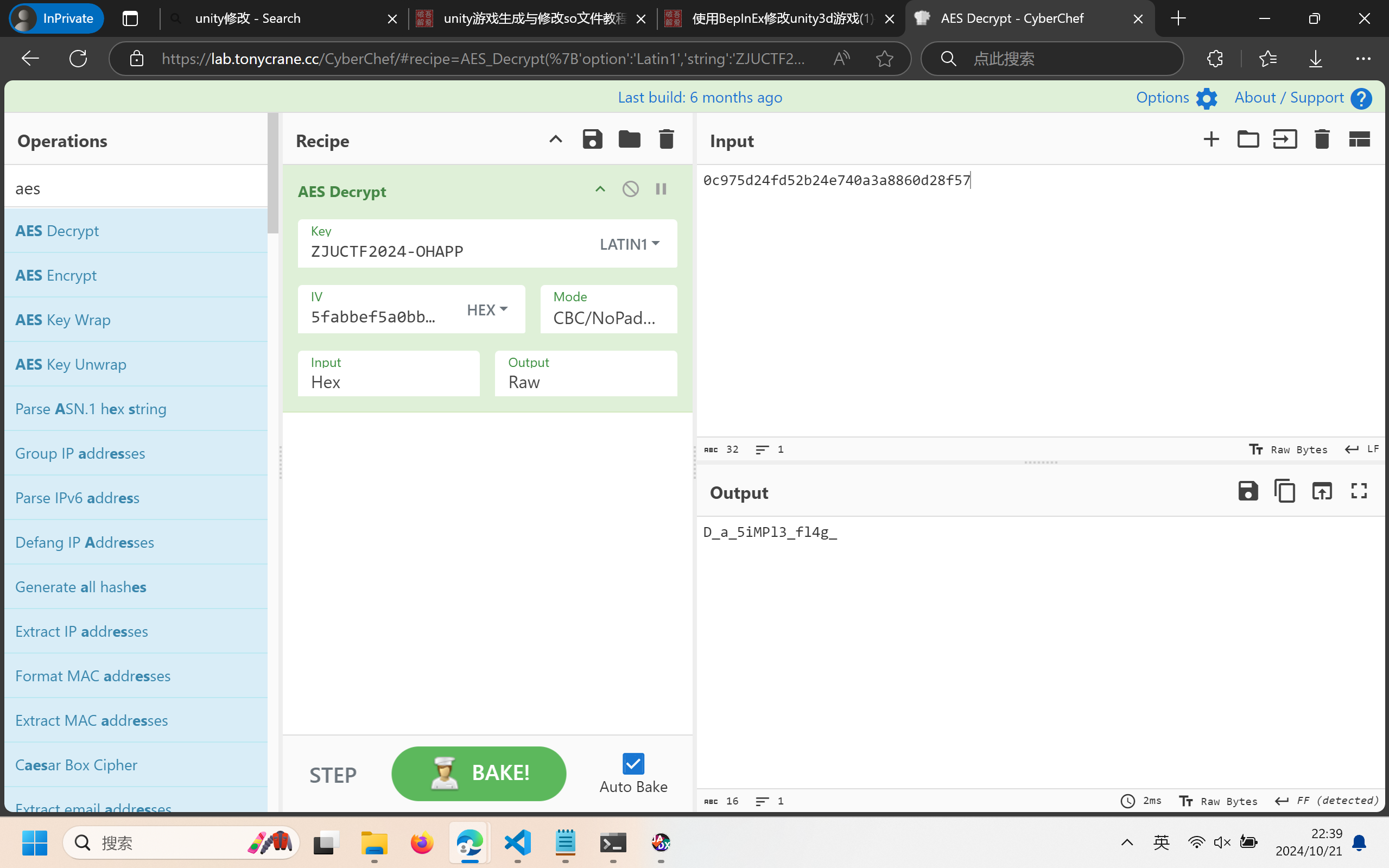
public Object CipherUtil(Object functionObject, Object newTarget, CipherUtil this) {
this.cipherAlgName = "AES128";
this.cipherAlgX = "AES128|ECB|NoPadding";
this.cipherAlgY = "AES128|CBC|NoPadding";
this.commonCipherKeyStr = "ZJUCTF2024-OHAPP";
this.init();
return this;
}
public Object func_main_0(Object functionObject, Object newTarget, CipherUtil this) {
Object CipherUtil = hole.CipherUtil(Object2, Object3, hole, ["init", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.init", 0, "encryptX", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.encryptX", 1, "encryptY", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.encryptY", 2, "encodeX", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.encodeX", 2, "encodeY", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.encodeY", 1, "encrypt", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.encrypt", 1, "stringToUint8Array", "com.zjuctf2024.easyhap/entry/ets/cipherUtil/CipherUtil.stringToUint8Array", 1, 7]);
Object obj = CipherUtil.prototype;
_module_0_ = CipherUtil;
return null;
}
public Object stringToUint8Array(Object functionObject, Object newTarget, CipherUtil this, Object arg0) {
Object buffer = import { default as buffer } from "@ohos:buffer";
return Uint8Array(buffer.from(arg0, "utf-8").buffer);
}
}
|